Vulnerability Categories
The vulnerabilities found in the OWASP Juice Shop are categorized into several different classes. Most of them cover different risk or vulnerabiliy types from well-known lists or documents, such as OWASP Top 10 or MITRE's Common Weakness Enumeration. The following table presents a mapping of the Juice Shop's categories to OWASP and CWE (without claiming to be complete).
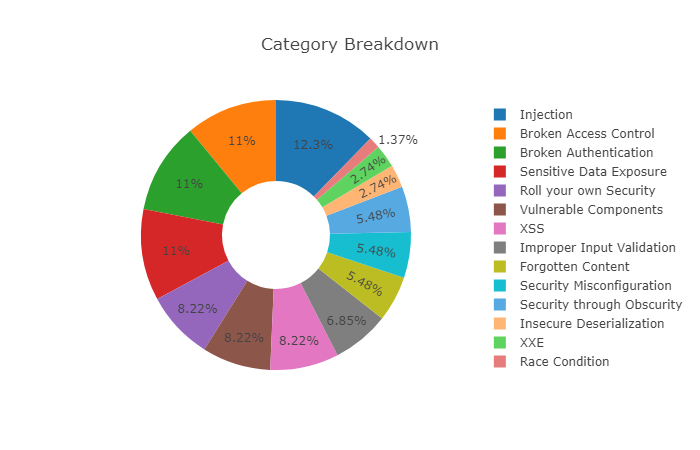
Category Mappings
| Category | OWASP | CWE |
|---|---|---|
| Injection | A1:2017 | CWE-74 |
| Broken Authentication | A2:2017 | CWE-287, CWE-352 |
| Forgotten Content | OTG-CONFIG-004 | |
| Roll your own Security | A10:2017 | CWE-326, CWE-601 |
| Sensitive Data Exposure | A3:2017 | CWE-200, CWE-327, CWE-328, CWE-548 |
| XML External Entities (XXE) | A4:2017 | CWE-611 |
| Improper Input Validation | ASVS V5 | CWE-20 |
| Broken Access Control | A5:2017 | CWE-22, CWE-285, CWE-639 |
| Security Misconfiguration | A6:2017 | CWE-209 |
| Cross Site Scripting (XSS) | A7:2017 | CWE-79 |
| Insecure Deserialization | A8:2017 | CWE-502 |
| Vulnerable Components | A9:2017 | |
| Security through Obscurity | CWE-656 | |
| Race Condition | OWASP-AT-010) | CWE-362 |